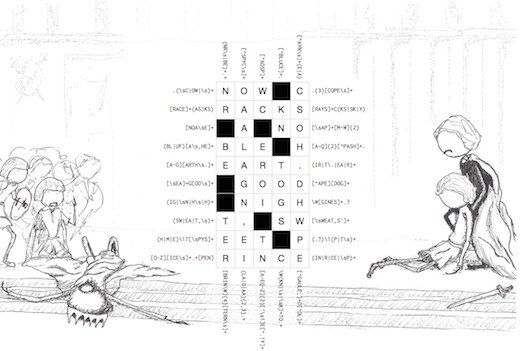
Christmas Run
Run #9 around Centennial Park. Two rounds again, this time during noon with some nice sun and a whopping 30°C :-)
Run #9 around Centennial Park. Two rounds again, this time during noon with some nice sun and a whopping 30°C :-)
Run #8 around Centennial Park. Two rounds again, and with some rain :-(
Run #7 around Centennial Park. Only one round, but the fastest one so far.
Run #6 around Centennial Park. Two rounds this time, with a slower pace though.
Run #5 around Centennial Park. Didn't have the patience to wait for the GPS to lock onto the signal, thus the late start.
Run #4 around Centennial Park, this time a bit later and thus with more sun:
Another run around Centennial Park, this time counterclockwise:
Next run around the beautiful Centennial Park:
The nice thing of being in Sydney during December is that you can go running during christmas time and it is 22°C :-)