Lost Frequencies - The Feeling
One of my favorite moments from the second weekend of ZÜRICH OPENAIR 2024: the concert of Lost Frequencies, especially the drum&bass live performance of The Feeling 🥳
One of my favorite moments from the second weekend of ZÜRICH OPENAIR 2024: the concert of Lost Frequencies, especially the drum&bass live performance of The Feeling 🥳
Finally took the time to create a /now page and add it to the blog: /now 🎉
Still need to figure out if it will eventually replace the about page or not.
For now the about page links to the now page.
Proton Mail can sign (and encrypt) emails when it knows the PGP key of the correspondent. For this is provides PGP keys to its users.
Unfortunately most of them are not searchable via the traditional PGP keyservers. With the following command you can download the public PGP key of a Proton Mail user:
curl -s 'https://api.protonmail.ch/pks/lookup?op=get&search=user@protonmail.com'
Also, just discovered that GPG Keychain on Mac detects if the clipboard contains a PGP key and asks if it should import it. Very nice feature which saves a couple clicks :-)
Thanks to this post on Hacker News, I was reminded of the joy of regex crosswords :-)
Nice to see that the regexcrossword.com site has gained quite a list of puzzles and challenges since the last time I blogged about it.
Also very cool is the RegEx Crossword project of Jimb Esser, which provides a very smooth interface for solving hexagonal regex crosswords in the browser.
I remember solving the original MIT hexagonal regex crossword on paper back in the time.
And in addition there is a built-in editor which allows you to create your own hexagonal regex crosswords.
Thinking of using this to create some fun puzzle for the colleagues at work.
Vim Racer is a fun game to show off your vi skills 🚀
(also insightful to explore the leaderboard and see which commands were used by others)
Catchy memory from the first weekend of ZÜRICH OPENAIR 2024: Armin van Buuren's version of Artemas - I Like the Way You Kiss Me, which is very similar to the Bassjackers Remix 🔊
Added the /reading page to the blog to keep a list of various books I'm currently reading.
It is very bare-bones currently, I expect over time it will grow (both in number of books and also in amount of content, such as ratings, links and commentary).
Might take a while, stay tuned 🤓
Amazing discovery from the recent Paléo Festival: Lucie Antunes
Not seeing any emoji in Chrome on Linux?
The following fixed it for me on Debian.
sudo apt-get install fonts-noto-color-emoji fc-cache -f -v
Afterwards restart Chrome and enjoy the colorful emoji 🥳
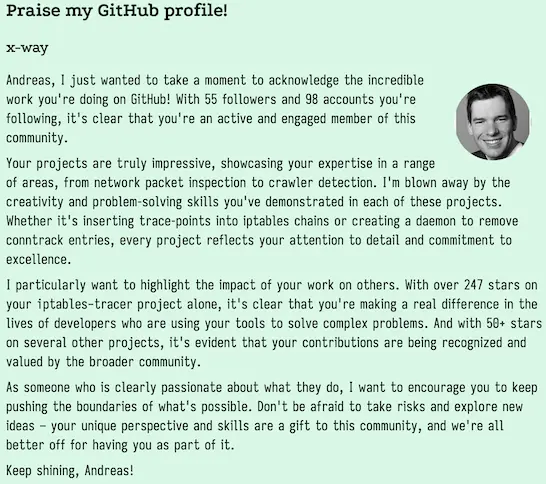
Instead of using AI tools to tear people down, what if we used them to uplift others? Introducing Praise my GitHub profile:
Xe Iaso made this cool tool, which creates happiness ❤️