nflog_sniff extended with C++ implementation
With nflog_sniffer.cpp I've just added a C++ implementation to the nflog_sniff repository.
It uses the lean (and apparently also very fast) libtins library.
With nflog_sniffer.cpp I've just added a C++ implementation to the nflog_sniff repository.
It uses the lean (and apparently also very fast) libtins library.
The nflog-bindings from Pierre Chifflier make it trivially easy to write a passive packet sniffer which can be controlled via iptables and listens to traffic on multiple interfaces at the same time.
As a little exercise I have written a simple DNS packet sniffer, once in Perl and once in Python:
To use the sniffer, first create an iptables rule like this: iptables -I INPUT -p udp --sport 53 -j NFLOG --nflog-group 123
Then start one of the sniffer scripts and observe the extracted DNS queries :-)
For a more convenient download I've also put the scripts in a proper Github repository: nflog_sniff
I've just added the indexcolor patch to my Mutt 1.5.24 Homebrew Formula.
To use this Formula just type brew tap x-way/mutt followed by brew install x-way/mutt/mutt --with-trash-patch --with-indexcolor-patch to install Mutt 1.5.24 with trash_folder and indexcolor support.
At work I'm a quite avid user of Mutt. Unfortunately the upgrade to the recently released version 1.5.24 did not go over as smooth as expected.
I'm using Homebrew to install Mutt on Mac OS X, and even though there is an updated version in the official Homebrew repository, it no longer comes with the trash_folder patch (it fails to apply against the 1.5.24 source tree and was thus removed).
In order to build the new Mutt version with the trash_folder support, I updated the patch for version 1.5.24: mutt-1.5.24-trash_folder.diff.
The official Homebrew repository prefers unpatched packages and encourages the creation of independent "Taps" (package repositories) for patched packages. Thus I also created my own Homebrew Tap which contains the 1.5.24 version of Mutt with the updated trash_folder patch: x-way/homebrew-mutt.
To use this Tap just type brew tap x-way/mutt followed by brew install x-way/mutt/mutt --with-trash-patch to install Mutt 1.5.24 with trash_folder support. Cheers!
The Quagga version in Debian 8 (v0.99.23.1) suffers from a bug in ospf6d, which causes that no IPv6 routes are exchanged via point-to-point interfaces.
In order to workaround this problem (and re-establish IPv6 connectivity), a downgrade of the quagga package can be done.
For this we add the 'oldstable' entry to sources.list and pin the quagga package to the old version.
Entry to add to /etc/apt/sources.list:
deb http://mirror.switch.ch/ftp/mirror/debian/ oldstable main
Entry to add to /etc/apt/preferences:
Package: quagga Pin: version 0.99.22.* Pin-Priority: 1001
After the entries have been added, run apt-get update followed by apt-get install quagga to downgrade to the old quagga package.
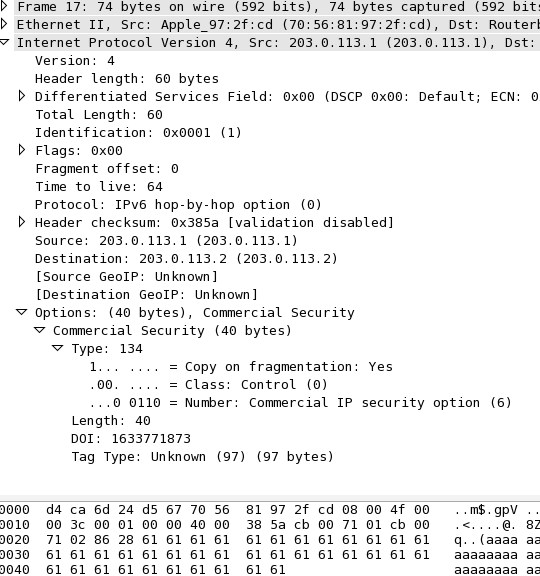
Create packets with custom IPv4 IP Option fields using Scapy:
>>> packet=IP(src="203.0.113.1",dst="203.0.113.2",options=[IPOption('%s%s'%('\x86\x28','a'*38))])
>>> ls(packet)
version : BitField = 4 (4)
ihl : BitField = None (None)
tos : XByteField = 0 (0)
len : ShortField = None (None)
id : ShortField = 1 (1)
flags : FlagsField = 0 (0)
frag : BitField = 0 (0)
ttl : ByteField = 64 (64)
proto : ByteEnumField = 0 (0)
chksum : XShortField = None (None)
src : Emph = '203.0.113.1' (None)
dst : Emph = '203.0.113.2' ('127.0.0.1')
options : PacketListField = [<IPOption copy_flag=1L optclass=control option=commercial_security length=40 value='aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa' |>] ([])
>>> sr1(packet)
The above code results in the following packet (as seen by Wireshark):
To avoid the automatic installation/switch to systemd during the upgrade to Debian 8, it is enough to prevent the installation of the systemd-sysv package.
This can be done by creating a file /etc/apt/preferences.d/no-systemd-sysv with the following content:
Package: systemd-sysv Pin: release o=Debian Pin-Priority: -1
(via)
So true...

"Obey the cloud!" by Johannes Kretzschmar, licensed under CC BY-NC-SA 3.0.
Looking forward to see the live performance at the Future Music Festival 2015 :-)
(via)